Tuesday, October 10, 2017 At 7:45AM
If you run into a .NET application you sometimes end up with some not very well known protocols like WCF Binary protocol or, in a recent case, a Fast Infoset binary encoding – a binary encoding of the XML Infoset and an alternative to the usual text-based XML Infoset encoding. We will briefly describe the Fast Infoset format and present a Burp plugin, which facilitates pentesting web applications using this XML representation.
Fast Infoset is a lossless compression format for XML-based data. The format is mostly utilised in web applications that transfer a large amount of data between a client and a server; usually a thick client processing data offline and exchanging data infrequently with a server. You can identify that Fast Infoset is involved when an HTTP request uses a Content-Type of application/fastinfoset.
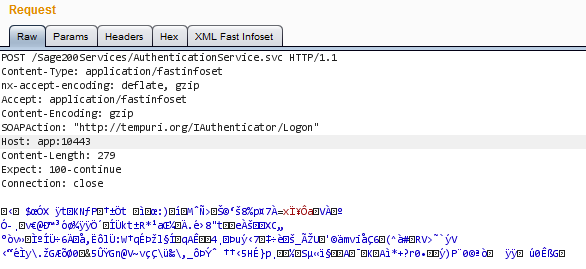
An example request may look like this:
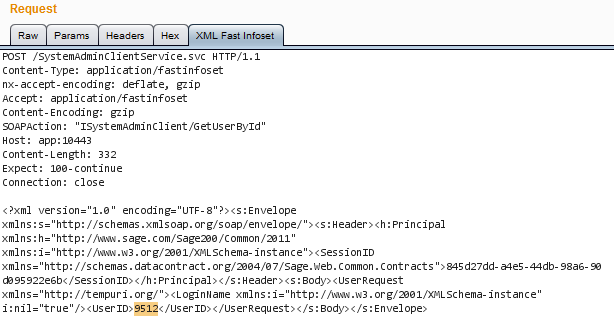
If you decompress the body with gzip, it is a little bit more readable.
From an attacker’s perspective, the main problem with this encoding format is that you can’t easily edit requests or responses on-the-fly like you would with text-based message bodies.Since the encoding relies on the previous and following strings, if you try to tamper with the data, the server will throw an exception saying that the data which you just have sent it is not properly encoded.
Some quick research revealed a few public repositories implementing Fast Infoset decoding but only one was working properly (written by Lu Jun). However, this plugin does not support editing and re-encoding decoded Fast Infoset data, only viewing it.
We decided it would be a worthwhile effort to develop a fully working Burp plugin for decoding and encoding Fast Infoset based requests. You can find a compiled JAR and the corresponding source code in the following Github repository:
https://github.com/GDSSecurity/FastInfoset-Burp-Plugin
Once you load the plugin via Burp extender, you can easily view decoded Fast Infoset requests and responses, and tamper with them in Burp Proxy and Repeater.
Author: Krzysztof Wegrzynek
©Aon plc 2023