The Cyber Loop
A Model for Sustained Cyber Resilience
The Cyber Loop
A Model for Sustained Cyber Resilience
Uniting stakeholders irrespective of role to make better decisions on cyber risk.
Download the paperThere is Nothing Linear About Cyber Security
Business and IT leaders are under increasing pressure to maximize return on security investment (ROSI) in an increasingly complex business and risk environment.
There is Nothing Linear About Cyber Security
Business and IT leaders are under increasing pressure to maximize return on security investment (ROSI) in an increasingly complex business and risk environment.
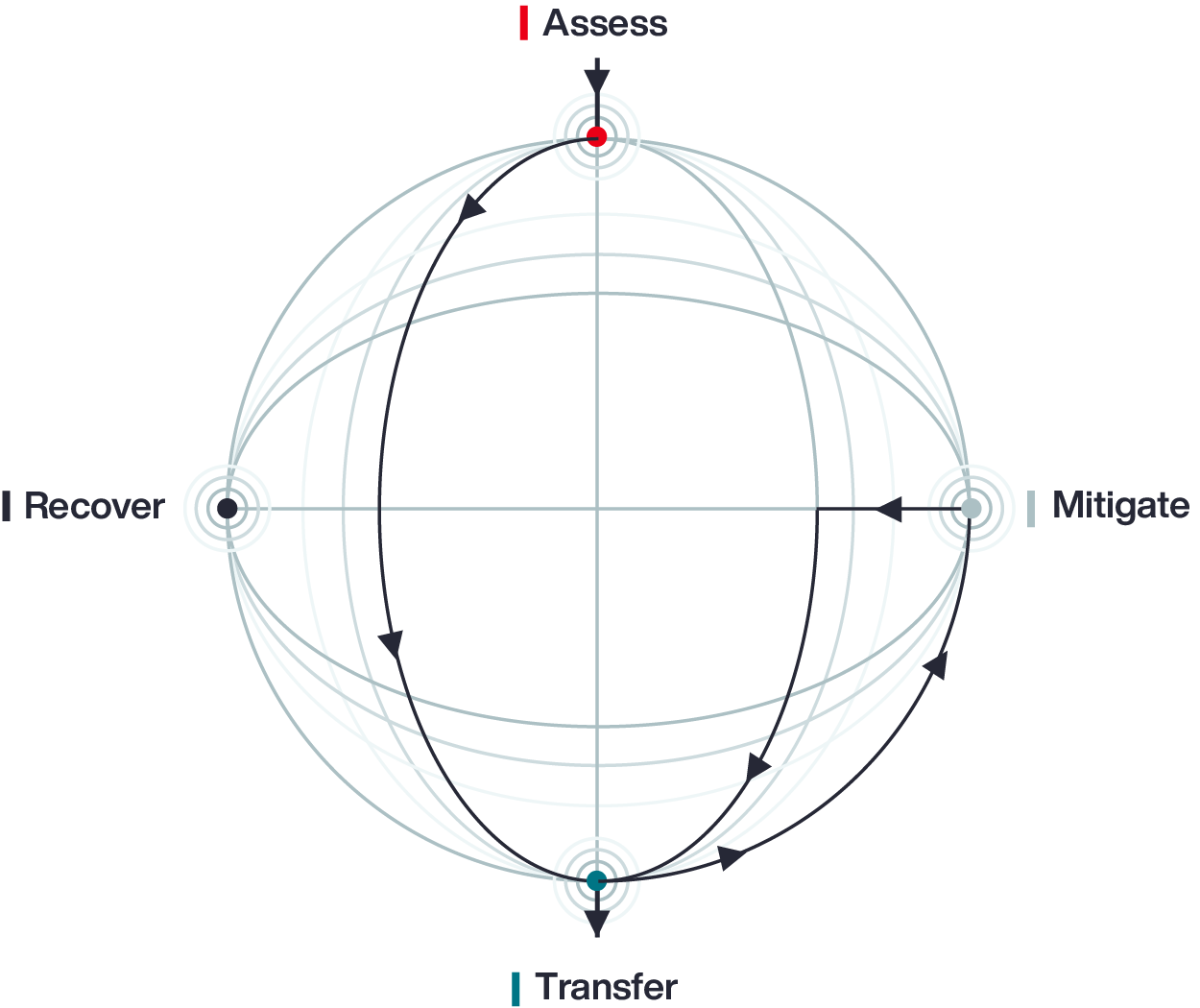
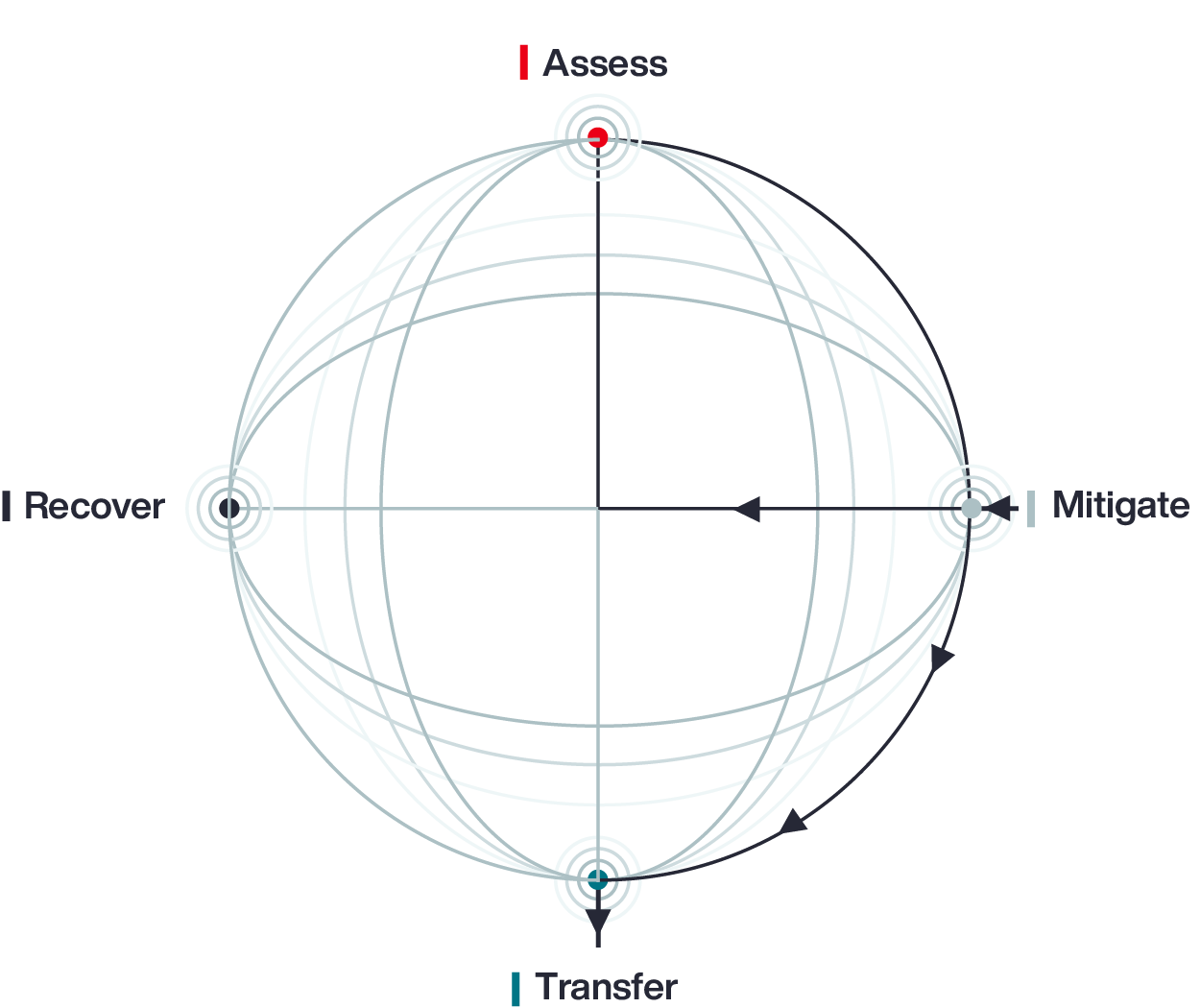
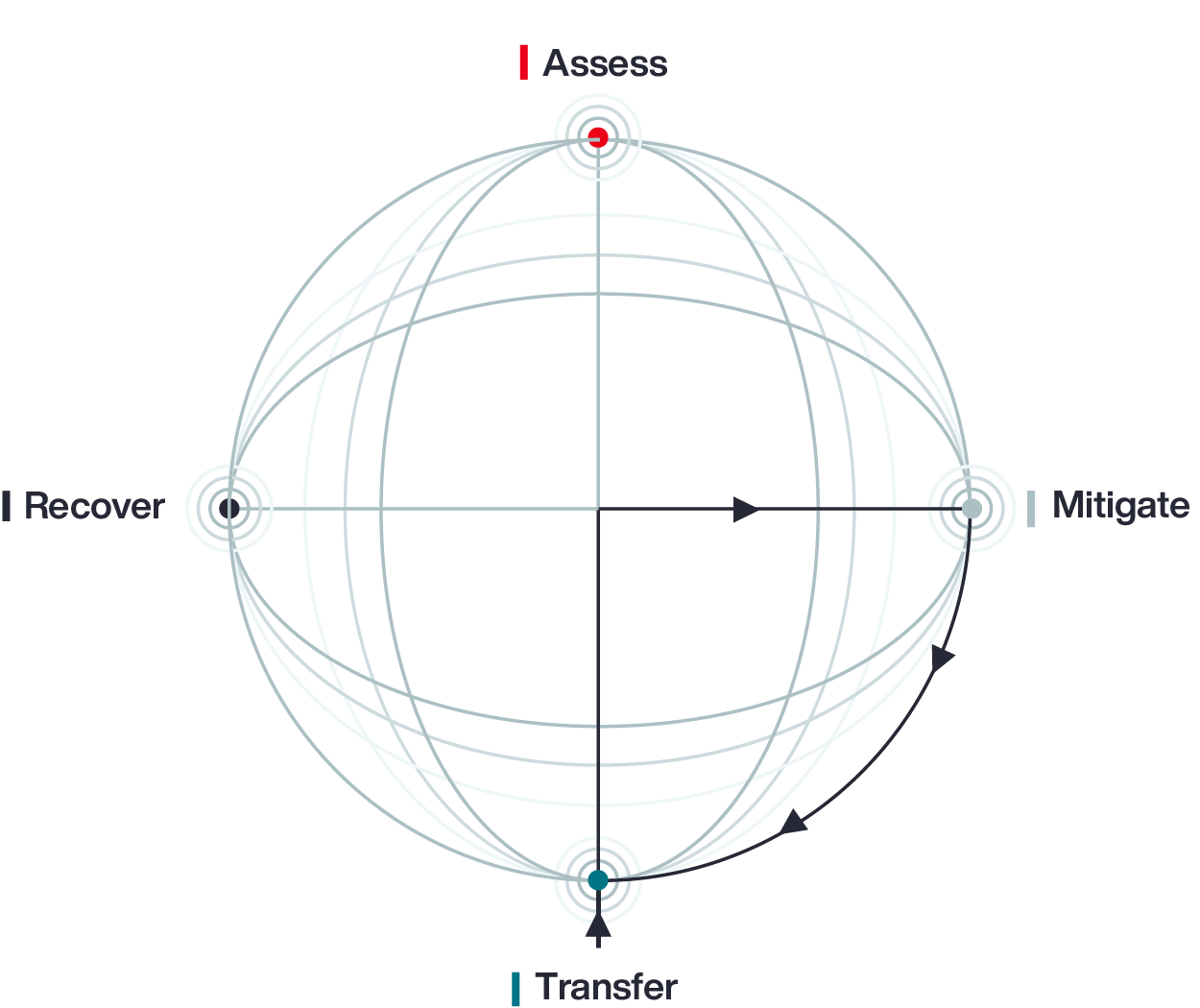
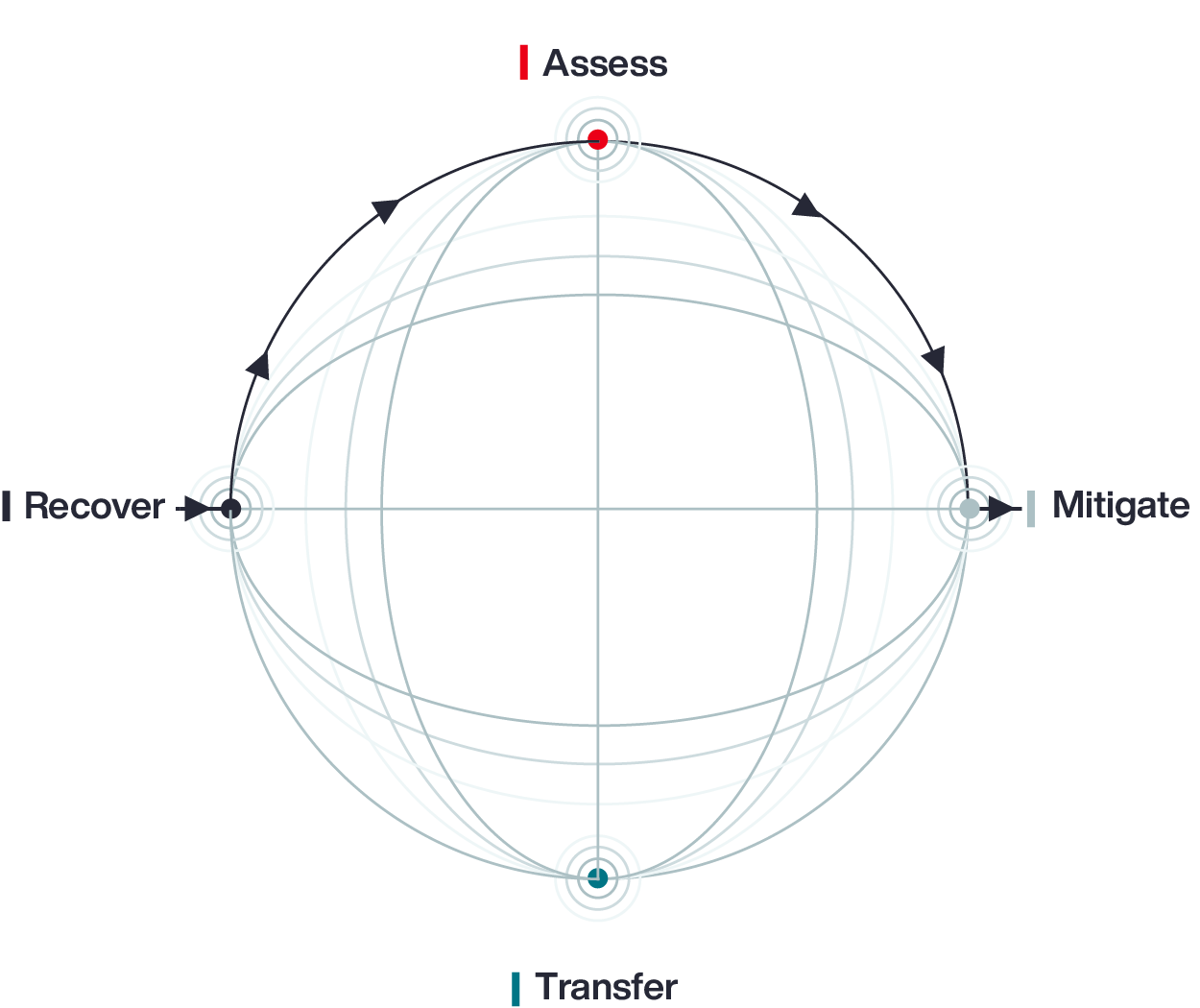
Aon’s Cyber Loop model acknowledges that each organization will start its journey from a different place: assess, mitigate, transfer, or recover. Once within the Loop, businesses become informed participants in managing risk, engaged in continuous review, improvement, and investment in security – guided by data.
Do you know the total cost of cyber risk to your organization?
Do you have access to data and financial modeling tools to measure your organization’s ROSI?
The Cyber Loop
A Model for Sustained Cyber Resilience
Eight Actions Your Organization Can Take Today To Reinforce Its Cyber Security Strategy
Review business continuity and disaster recovery (BCDR) plans to ensure they take account of, and regularly test for, cyber threats.
Assess vulnerabilities.This allows organizations to strategically budget and address critical areas.
Review governance, controls, roles, and responsibilities and develop protective safeguards to prevent ransomware attacks.
Quantify the financial loss associated with an incident, breach, or disruption.
Engage in breach simulations and tabletop exercises to test incident preparedness.
Check contractual protections and have all insurance policies reviewed to ensure the organization is covered for financial loss from a breach.
Proactively utilize threat intelligence to monitor for the tactics, techniques, and procedures (TTPs) of cyber attackers.
Never stop cycling through The Cyber Loop.
Businesses circle through Cyber Loop entry points — to achieve sustained resilience. Stakeholders come together to assess where they sit in the circular journey.
Better decisions around cyber risk are made.
Case In Point
Explore case examples by clicking on the Cyber Loop entry points below.
- Assess
- Mitigate
- Transfer
- Recover
Case In Point
Explore case examples by clicking on the Cyber Loop entry points below.
- Assess
- Mitigate
- Transfer
- Recover

It’s time to become an informed participant in managing risk.
To realize the promise of The Cyber Loop, it is critical that stakeholders – across the business – come together to assess where they sit in the circular cyber resilience journey. Harness the value of data to make better decisions.